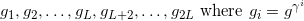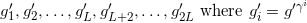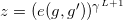Name: Anonymous Credential Protocol
Author: Mike Lodder and Brent Zundel
Start Date: January 25, 2019
Status¶
Status: ADOPTED
Status Date: implemented in mid 2018
Status Note: implemented in libindy
Summary¶
Anonymous credentials form the heart of Indy’s identity capabilities. This document describes the protocol for Camenisch-Lysyanskaya signatures and the anonymous credentials they enable.
This document is a markdown-formatted version of work by Dmitry Khovratovich, which is based on CL signatures. The latex source used for the equations in this version may be found here.
Motivation¶
This HIPE is intended as a publication of the protocol behind the code that has already been implemented in indy-crypto.
Tutorial¶
Introduction¶
Concept¶
Anonymous credentials allow an identity owner to prove certain properties about their identity an uncorrelatable way without revealing other identity details. The properties can be raw identity attributes such as a birth date or address, or more sophisticated predicates such as “A is older than 20 years old”.
We assume three parties: issuer, holder, and verifier. From the functional perspective:
the issuer gives a credential C based on identity schema X, which asserts certain properties 𝒫 about X, to the holder.
The credential consists of attributes represented by integers m1, m2,…, ml.
The holder then presents (𝒫,C) to the verifier, which can verify that the issuer has asserted property 𝒫.
Properties¶
Credentials are unforgeable in the sense that no one can fool the verifier with a credential not prepared by the issuer.
Credentials are unlinkable in the sense that it is impossible to correlate the presented credential across multiple presentations. This is implemented by the holder proving with a zero-knowledge proof that he has a credential rather than showing the credential. Unlinkability can be simulated by the issuer generating a sufficient number of ordinary unrelated credentials.
Note: unlinkability may be turned off to make credentials one-time use so that second and later presentations are detected.
Generic notation¶
Attribute m is a la-bit unsigned integer. Technically it is possible to support credentials with different la, but in Sovrin it is set la=256.
Protocol Overview¶
The described protocol supports anonymous credentials given to multiple holders by various issuers, which are presented to various relying parties.
Various types of anonymous credentials can be supported. In this section, the combination of CL-based credentials and pairing-based revocation is described.
The simplest credential lifecycle, with one credential, single issuer, holder, and verifier is as follows:
Issuer determines a credential schema 𝒮: the type of cryptographic signatures used to sign the credentials, the number l of attributes in a credential, the indices Ah ⊂ {1,2,…,l} of hidden attributes, the public key Pk, the non-revocation credential attribute number lr and non-revocation public key Pr (Section~\ref{sec:iss-setup}). Then he publishes it on the ledger and announces the attribute semantics.
Holder retrieves the credential schema from the ledger and sets the hidden attributes.
Holder requests a credential from issuer. He sends hidden attributes in a blinded form to issuer and agrees on the values of known attributes Ak = {1,2,…,l} \ Ah.
Issuer returns a credential pair (Cp, CNR) to holder. The first credential contains the requested l attributes. The second credential asserts the non-revocation status of the first one. Issuer publishes the non-revoked status of the credential on the ledger.
Holder approaches verifier. Verifier sends the Proof Request ℰ to holder. The Proof Request contains the credential schema 𝒮E and disclosure predicates 𝒟. The predicates for attribute m and value V can be of form m=V, m<V, or m>V. Some attributes may be asserted to be the same: mi=mj.
Holder checks that the credential pair he holds satisfies the schema 𝒮E. He retrieves the non-revocation witness from the ledger.
Holder creates a proof P that he has a non-revoked credential satisfying the proof request ℰ and sends it to verifier.
Verifier verifies the proof.
If there are multiple issuers, the holder obtains credentials from them independently. To allow credential chaining, issuers reserve one attribute (usually m1) for a secret value hidden by holder. The holder is supposed then to set it to the same hidden value in all issued credentials. Relying Parties require them to be the same in all credentials. A proof request should specify the list of schemas that credentials should satisfy in.
Schema preparation¶
Credentials may have limited use to only authorized holder entities called agents. Agents can prove authorization to use a credential by the holder including a policy address I in primary credentials as attribute m3.
Attributes¶
Issuer defines the primary credential schema 𝒮 with l attributes m1,m2,…, ml and the set of hidden attributes Ah ⊂ {1,2,…,l}.
By default, {1,3} ⊂ Ah whereas 2 ∉ Ah
Issuer defines the non-revocation credential with 2 attributes m1,m2.
In Sovrin:
Ah = {1} and m1 is reserved for the link secret of the holder,
m2 is reserved for the context – the enumerator for the holders,
m3 is reserved for the policy address I.
Primary Credential Cryptographic Setup¶
In Sovrin, issuers use CL-signatures for primary credentials.
For the CL-signature, the issuer generates:
Random 1536-bit primes p’,q’ such that p ← 2p’+1 and q ← 2q’+1 are also prime. Then computes n ← pq.
A random quadratic residue S mod n;
Random
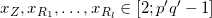 xZ, xR1,...,xRl ∈ [2; p'q'-1]
xZ, xR1,...,xRl ∈ [2; p'q'-1]
Issuer computes:
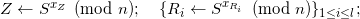 Z ← SxZ(mod n); {Ri ← SxRi(mod n)}1 ≤ i ≤ l;
Z ← SxZ(mod n); {Ri ← SxRi(mod n)}1 ≤ i ≤ l;
The issuer’s public key is
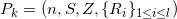 Pk = (n, S,Z,{Ri}1 ≤ i ≤ l)
and the private key is sk = (p, q).
Pk = (n, S,Z,{Ri}1 ≤ i ≤ l)
and the private key is sk = (p, q).
Issuer Setup Correctness Proof¶
Issuer generates random
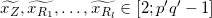 x~Z, x!R1,...,x~Rl ∈ [2; p'q'-1]
x~Z, x!R1,...,x~Rl ∈ [2; p'q'-1]Computes:
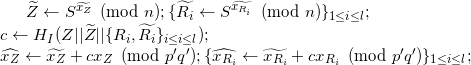
Here HI is the issuer-defined hash function, by default SHA2-256.
Proof 𝒫I of correctness is
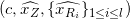
Non-revocation Credential Cryptographic Setup¶
In Sovrin, issuers use CKS accumulators and signatures to track revocation status of primary credentials, although other signature types will be supported too. Each primary credential is given an index from 1 to L.
The CKS accumulator is used to track revoked primary credentials, or equivalently, their indices. The accumulator contains up to L indices of credentials. If issuer has to issue more credentials, another accumulator is prepared, and so on. Each accumulator A has an identifier IA.
Issuer chooses:
Groups 𝔾1,𝔾2,𝔾T of prime order q
Type-3 pairing operation e: 𝔾1 x 𝔾2 → 𝔾T.
Generators: g for 𝔾1, g’ for 𝔾2.
Issuer:
Generates
Random
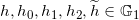
Random
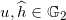
Random sk, x (mod q).
Computes
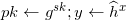
The revocation public key is
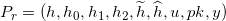 and the secret key is (x,sk).
and the secret key is (x,sk).
New Accumulator Setup¶
To create a new accumulator A, issuer:
Generates random γ (mod q).
Computes
Set V ← ∅, acc ← 1
The accumulator public key is Pa = z and secret key is γ.
Issuer publishes (Pa,V) on the ledger. The accumulator identifier is IDa = z.
Issuance of Credentials¶
Holder Setup¶
Holder:
Loads credential schema 𝒮.
Sets hidden attributes { mi }{i ∈ Ah}.
Establishes a connection with issuer and gets nonce n0 either from issuer or as a precomputed value. Holder is known to issuer with identifier ℋ.
Holder prepares data for primary credential:
Generate random 3152-bit v’.
Generate random 593-bit {m̃i}{i ∈ Ah}, and random 3488-bit ṽ’.
Compute, taking S,Z,Ri from Pk:
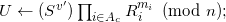
Compute
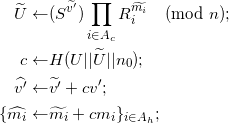
Generate random 80-bit nonce n1
Send to the issuer:
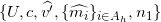
Holder prepares for non-revocation credential:
Load issuer’s revocation key PR and generate random s’Rmod q.
Compute UR ← h2s’R taking h2 from PR.
Send UR to the issuer.
Issuer Proof of Setup Correctness¶
To verify the proof 𝒫i of correctness, holder computes:
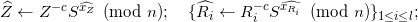
and verifies
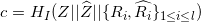
Primary Credential Issuance¶
Issuer verifies the correctness of holder’s input:
Compute
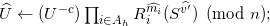
Verify c = H( U || Û || n0 )
Verify that v̂’ is a 673-bit number, {m̂i r̂i}i ∈ 𝒜c are 594-bit numbers.
Issuer prepares the credential:
Assigns index i<L to holder, which is one of not yet taken indices for the issuer’s current accumulator A. Compute m2← H(i||ℋ) and store information about holder and the value i in a local database.
Set, possibly in agreement with holder, the values of disclosed attributes, i.e. with indices from Ak.
Generate random 2724-bit number v’’ with most significant bit equal 1 and random prime e such that 2596≤ e ≤ 2596 + 2119
Compute
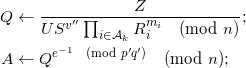
Generate random r < p’q’;
Compute
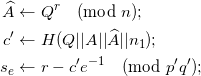
Send the primary pre-credential ( {mi}i ∈ Ak, A, e, v’’, se, c’ ) to the holder.
Non-Revocation Credential Issuance¶
Issuer:
Generate random numbers s’’, c mod q.
Take m2 from the primary credential he is preparing for holder.
Take A as the accumulator value for which index i was taken. Retrieve current set of non-revoked indices V.
Compute:
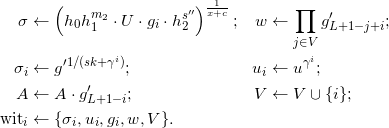
Send the non-revocation pre-credential ( IA, σ, c, s’’, witi, gi, gi’, i ) to holder.
Publish updated V, A on the ledger.
Storing Credentials¶
Holder works with the primary pre-credential:
Compute v ← v’+v’’.
Verify e is prime and satisfies 2596≤ e ≤ 2596 + 2119
Compute
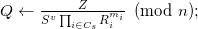
Verify Q = Ae mod n
Compute
 ← Ac’ + se * emod n
Verify c’ = H( Q || A || Â || n2 ).
Store primary credential Cp = ( { mi }i ∈ Cs, A, e, v ).
Holder takes the non-revocation pre-credential ( IA, σ, c, s’’, witi, gi, gi’, i) computes sR ← s’+s’’ and stores the non-revocation credential CNR ← ( IA, σ, c, s, witi, gi, gi’, i).
Non revocation proof of correctness¶
Holder computes:
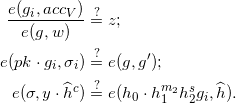
Revocation¶
Issuer identifies a credential to be revoked in the database and retrieves its index i, the accumulator value A, and valid index set V. Then he proceeds:
Set V ← V \ {i};
Compute A ← A/g’L+1-i
Publish {V,A}.
Presentation¶
Proof Request¶
Verifier sends a proof request, where it specifies the ordered set of d credential schemas { 𝒮1, 𝒮2, …, 𝒮d }, so that the holder should provide a set of d credential pairs ( Cp, CNR ) that correspond to these schemas.
Let credentials in these schemas contain X attributes in total. Suppose that the request is made:
to reveal x1 attributes,
to prove x2 equalities mi = mj (from possibly distinct schemas)
to prove x3 predicates of form mi > ≥ ≤ < z.
Then effectively X - x1 attributes remain hidden (denoted Ah), which form x4 = (X - x1 - x2) equivalence classes.
Let ϕ map Ah to { 1, 2, …, x4 } according to this equivalence.
Let Av denote the set of indices of x1 attributes that are disclosed.
The proof request also specifies Ah, ϕ, Av and the set 𝒟 of predicates. Along with a proof request, the verifier also generates and sends an 80-bit nonce n1.
Proof Preparation¶
Holder prepares all credential pairs
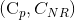 to submit:
to submit:
Generates x4 random 592-bit values $ỹ1, ỹ2,…,ỹx4 and set
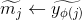 for
for 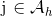 .
.Create empty sets 𝓣 and 𝓒.
For all credential pairs
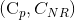 execute Proof Preparation.
execute Proof Preparation.Executes hashing once.
For all credential pairs
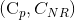 execute Final Preparation.
execute Final Preparation.Executes Final Preparation once.
Verifier:
For all credential pairs
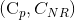 executes Verification.
executes Verification.Executes final hashing once.
Non-revocation proof¶
Holder:
Load issuer’s public revocation key
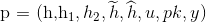 .
.Load the non-revocation credential
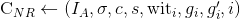 ;
;Obtain recent V, acc (from verifier, Sovrin link, or elsewhere).
Update
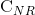 :
: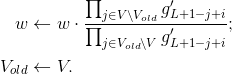
Here Vold is taken from witi and updated there.
Select random
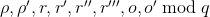 ;
;Compute
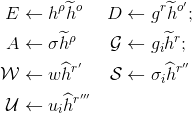
and adds these values to 𝓒.
Compute
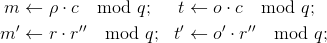
and adds these values to 𝓒.
Generate random
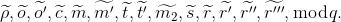
Compute
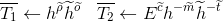
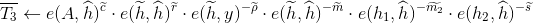
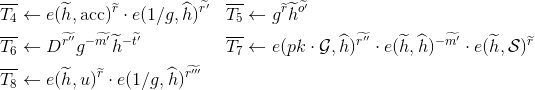
and add these values to 𝓣.
Validity proof¶
Holder:
Generate a random 592-bit number
 for each
for each
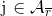 .
.For each credential
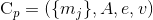 and issuer’s public key
and issuer’s public key 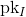 :
:Choose random 3152-bit r.
Take
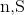 from
from
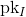 compute
compute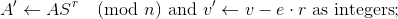
and add to 𝓒.
Compute
 .
.Generate random 456-bit number
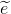 .
.Generate random 3748-bit number
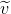 .
.Compute
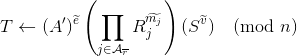
and add to 𝓣.
Load Z,S from issuer’s public key.
For each predicate p where the operator * is one of
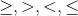 .
.Calculate
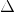 such that:
such that: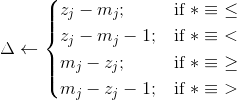
Calculate a such that:
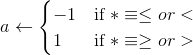
Find (possibly by exhaustive search)
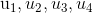 such that:
such that:
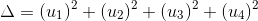
Generate random 2128-bit numbers
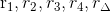 .
.Compute
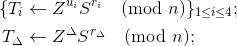 and add these values to 𝓒 in the order
and add these values to 𝓒 in the order
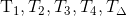 .
.Generate random 592-bit numbers
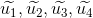 .
.Generate random 672-bit numbers
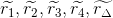 .
.Generate random 2787-bit number
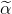
Compute
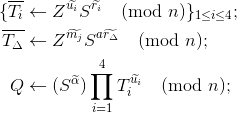
and add these values to 𝓣 in the order
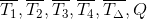 .
.
Hashing¶
Holder computes challenge hash
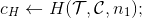
and sends cH to verifier.
Final preparation¶
Holder:
For non-revocation credential CNR compute:
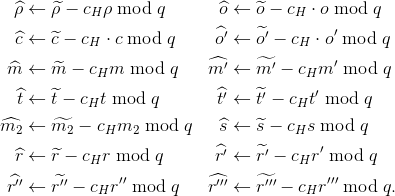
and add them to 𝓧.
For primary credential Cp compute:
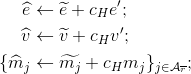
The values
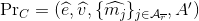 are the sub-proof for credential
Cp.
are the sub-proof for credential
Cp.For each predicate p compute:
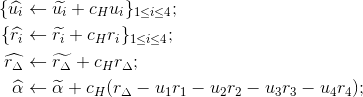
The values
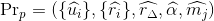 are the sub-proof for
predicate p.
are the sub-proof for
predicate p.
Sending¶
Holder sends (c,𝓧, {PrC}, {Prp}, 𝓒) to the verifier.
Verification¶
For the credential pair (Cp, CNR), verifier retrieves relevant variables from 𝓧, {PrC}, {Prp}, 𝓒.
Non-revocation check¶
Verifier computes:
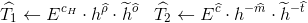
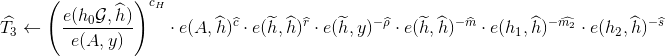
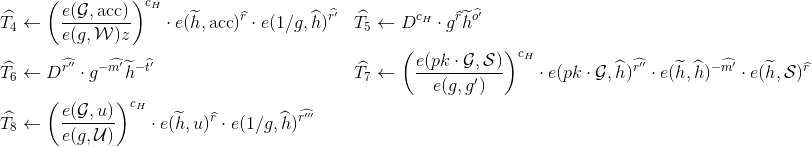
and adds these values to 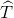 .
.
Validity¶
Verifier uses all issuer public key  involved
into the credential generation and the received
involved
into the credential generation and the received
 . He also uses revealed
. He also uses revealed
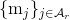 . He initiates
. He initiates
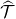 as an empty set.
as an empty set.
For each credential Cp, take each sub-proof PrC and compute:
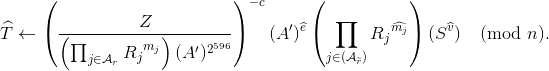
Add
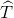 to
to
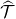 .
.For each predicate p:
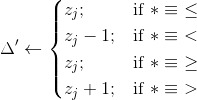
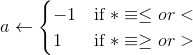
Using Prp and 𝓒 compute
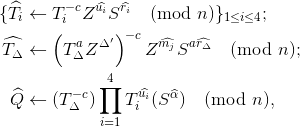
and add these values to
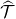 in the order
in the order
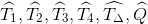 .
.
Final hashing¶
Verifier computes
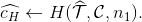
If
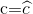 output VERIFIED else
FAIL.
output VERIFIED else
FAIL.
A Note About Encoding Attributes¶
The above protocol shows how a credential issuer may sign an array of attributes, which are defined as 256-bit integers. In order for the protocol to be used for credentials that contain attributes which are not integers, such as strings, it is necessary to encode those attributes as integers.
The current implementation of Indy-SDK allows for two types of values as attributes in credentials: integers and strings. The integers are used as is. The strings are hashed using SHA-256, and the resulting 256-bit integers are signed. While the protocol described in this paper is sufficient to prove that the integer presented to a verifier is the same one that an issuer signed, it is left to Indy-SDK to prove that the strings presented to a verifier, when hashed using SHA-256, are the same as the 256-bit integers which the issuer signed.
Reference¶
Drawbacks¶
One drawback to this approach is that the signatures for the primary credential are RSA-based. This results in keys and proofs that are much larger than other signature schemes would require for similar levels of expected security.
Another drawback is that revocation is handled using a different, elliptic-curve based signature that allows the use of the more-efficient set-membership proofs and accumulators required by that part of the protocol.
This dual-credential model provides all of the functionality required by the protocol, but uses two different signature schemes to accomplish it, one of which is based in outdated technology that requires very large keys and proofs. Using two signature types results in a more unwieldy protocol.
Rationale and alternatives¶
As this protocol is describes the current implementation, rationale and alternatives point necessarily to potential future work.
The dual-credential model is not ideal, so possible future anonymous credential schemes should strive to find a data structure and proof scheme that meets the required characteristics of selective disclosure of attributes, predicate proofs, and set membership proofs. It is outside of the scope of this document to speculate on what form those structures and proofs may take.
Prior art¶
It is the understanding of the authors that few production quality implementations of anonymous credential signature schemes exist.
Two implementations we are aware of are Idemix, implemented by IBM, and IRMA, implemented by The Privacy by Design Foundation.
Unresolved questions¶
This protocol is already implemented in indy-crypto.